Wargames, April 2025 – Command and Control (C2), Nimbo-C2
23 April
Nimbo-C2 is a lightweight server-client based framework that uses HTTP for the communications channel and a small (compiled on the server) agent to control the victims device with options for both Windows and Linux operating systems. Interestingly outside of the detection of the transfer of the executable and the HTTP connections there isn’t much to see from the network firewalls perspective – perhaps due to the use of common encryption frameworks and libraries which offer little by the way of anything ‘malicious to detect’.
A perfect demonstration that multiple layers of security are necessary to obtain effective coverage; I can imagine instances where a Linux webserver without an effective EDR agent installed and with an exploitable file upload/execution vulnerability are susceptible to further compromise with this C2 agent.
Getting setup
Unsurprisingly the server side is wrapped up in a easy to use Docker container; once the dependencies are built the threat actor simply needs to modify a single JSON file with the public address of the C2 server and set an encryption key.
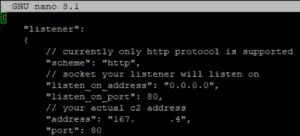
With the server started the command line interface is used to build the C2 client which in the case of the Windows version includes hooks into Event Tracing for Windows to help hide the agents activities as well as bypassing the Anti-Malware Scan Interface, while perhaps handy techniques to exploit – these activities raise instant red flags for any effective EDR agent.

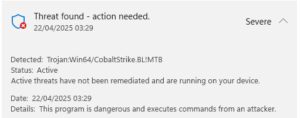
With the agent running on the victims device it was reassuring to see Defender pop up – as part of our usual process in Wargames we set all protections (network/device) to ‘alert only’ mode, after all with the extensive lists of exceptions in anti-malware agents (often including user writable folders or specific file names) that we keep seeing during the delivery of our Security Review service there is a realistic possibility that threat actors will get lucky and land their malware into one of these folders.
Impact
With the agent connected and calling back to our server it’s time to explore the capabilities including screenshot capture…
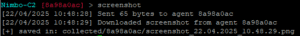
clipboard capture, file upload/download (although anything over 100mb in size seems to really hammer the RAM usage on the client), a keylogger, in memory PowerShell command execution and much more.
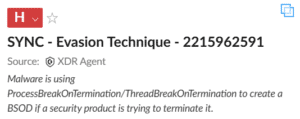
As a handy method of limiting the scope of forensic analysis the C2 agent loads itself into memory allowing the deletion of the initial executable, you can also mark the process it’s running under as critical such that the device blue screens if the execution is of the agent is terminated – perhaps a handy route to performing a bulk denial service attack as well. Again, as you might expect – effective EDR agents will detect the marking of the process as critical as a behavioural threat indicator.
With this broad range of capabilities you can envision how a threat actor would start using the initial foothold to perform Lateral Movement, identify Unsecured Credentials, and before you know it they are deleting backups and delivering ransomware.
The utility of Cyber Threat Intelligence (CTI) sharing between vendors
Perhaps the most interesting finding from this investigation is just how effective the sharing of Cyber Threat Intelligence between vendors is. On the first day of execution only 15 out of 72 anti-malware agents in VirusTotal detected my agent, running the same analysis the following day and that count is up to 36 anti-malware agents.
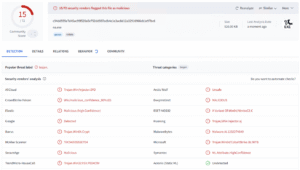
On the day of use

The following day
The responsive Security Operations Centre (SOC)
I’ve called out the use of exceptions in anti-malware agents in this article as something we keep seeing, and we truly do – perhaps the folder used by a MSP for software distribution (that’s also low privilege user writable), a folder that includes legacy software that ‘doesn’t play well’ with anti-malware agents, or in some cases PsExec.exe as a filename in any folder. Each of these exceptions represent an easy win for a threat actor who has the opportunity to perform any measure of resonance – or perhaps in the most extreme situations who has compromised SSO and is now inside the anti-malware console making changes that don’t generate admin alerts!
So the take away from this article – first review your anti-malware exceptions, while that’s underway have a chat with your SOC – what visibility into executions in this exception space do they have? Perhaps you are not in that privileged place to have a SOC service, well what then – how do you detect, prevent, alert and ultimately respond to such threats?
