Wargames, April 2025 – Command and Control (C2), Covenant C2
23 April
Introduction to Covenant
Covenant is a readily available C2 Framework that is built around ASP .NET Core and thus can be used to control Linux, Windows and Mac OS devices. A quick Google search returns downloads, source code and a wealth of documentation and tutorials for using Covenant. It is incredibly easy to set up and run, requiring very little skill or prior knowledge.
How Covenant Operates
During our testing, a Ubuntu server was created on a cloud hosted IaaS service. With just a few taps of the keyboard, following the handy provided step-by-step guide we were able to get our hostile infrastructure simulated within a few minutes.
The ease with which Covenant can then be set up and ready to use is quite astounding. A low-skilled threat actor is very likely to be able to create a C2 server in the cloud. Once the server is created, Covenant then provides a handy web-based GUI for interacting with Victims.

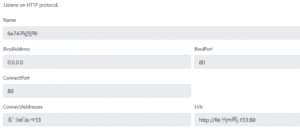
The server is set to “listen” for victims connections on a specified IP address and it’s ready to go!
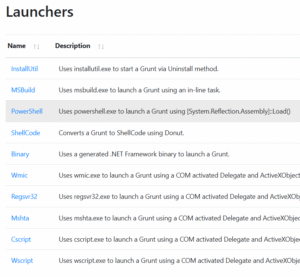
The threat actor then needs to infect their victims system with the covenant ‘grunt’ agent. Helpfully, covenant offers a range of options for doing this. In our testing, I used the “PowerShell” option which provides an encrypted PowerShell string to run on a victims machine. The quick and easy script based deployment makes Covenant a good candidate for introducing to an unsecured environment through something like the HAK5 Rubber Ducky that we explored in a previous ANSecurity Wargames session.
Assuming the Threat Actor is able find a method of infecting the victim, the ‘grunt’ machine then gives the Threat Actor a menu of oven-ready commands that can be executed on the victims computer. With attacks ranging from dumping credentials, spying on the users screen, creating new user accounts or running additional scripts it’s easy to see how this C2 tool can rapidly establish persistence and progress through the MITRE ATT&CK stages.
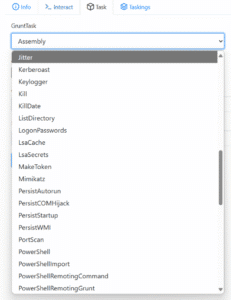
In testing, we were able to quickly obtain the systems administrator password as well as enumerate software, security products and services running. Additionally Covenant makes network reconnaissance and further escalation very easy for a low-skilled threat actor.
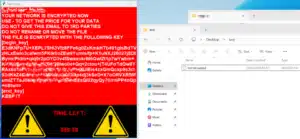
With a quick test of file transfer and additional scripts running options we were able to get ransomware onto the victim’s machine and encrypt a test folder in just a few minutes, with the decryption keys sent back through the C2 channel to me as the simulated Threat Actor.
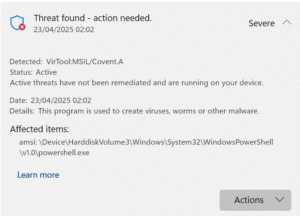
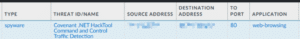
Detecting Covenant
In our testing, we found that Covenant could be detected with relative ease by behavioural analysis and real-time protections on our victims machine. Additionally, application aware firewalls should be able to recognise the C2 traffic and block it. In an environment without effective endpoint configuration hardening and EDR it’s easy to see how Covenant could remain undetected on a device and maintain persistence.