What happens when you ‘click the link’ part 2
06 October
Time to bump our threat actors up a notch – our previous SMS phishing example was well aligned to a casual threat actor, a spray and pray approach with no specific tuning or personalisation. In our next example we’re looking at a determined threat actor in that they’ve made some modifications to their phishing kit to go after ANSecurity specifically as well as made further use of legitimate services to help their phishing email make it’s way through filters and other security technologies.
While this email made it through our spam filters (through our own threat emulation service we’ve found it’s almost always possible to get just one through before ‘they adapt’) our targeted staff member quickly informed our internal IT security team (score 1 for security awareness training) and we instigated our process to review the email and perform log analysis to confirm that the message wasn’t interacted with.
Phishing for credentials via email
See https://app.any.run/tasks/e9daa471-379c-44a1-b032-1ff188faac2d for the sandbox investigation.
We see all the usual lures in this one, ‘Action required’, ‘salary compensation’, ‘eSignature’, a really well crafted email that looks professional even without allowing images to be displayed.
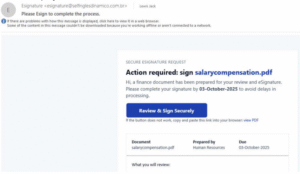
The threat actor had clearly gone to some lengths to help this domain deliver email – with both SPF and DKIM configured, a shame they couldn’t go all the way and just a shame that they didn’t also configure DMARC although they may not worry too much about others impersonating their domain! Either the threat actor is being very careful in the use of their domain or they are just getting lucky with 0 hits on VirusTotal (other than our own report!) so far.

Alongside the professional looking email we can see that the threat actor has picked themselves up an account with SendGrid account, luckily their abuse reporting system (a mailbox) is easy to work with! If we get something other than an automated response we will provide an update to this short story.
![]()
Alongside the SendGrid account it looks like the threat actor has managed to get some access to the legitimate Microsoft Dynamics service – perhaps a compromised account? Just a shame there isn’t very much we can use to report this one. Either way we’re back at a CAPTCHA to validate we’re human to attempt to evade automated analysis.
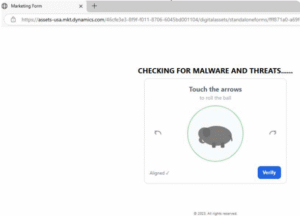
A brief hop/skip/jump through a ‘loading screen’ which attempts to build some trust by displaying the ansecurity.com domain, the browser and OS used, an attempt at geolocation (not that it’ll work from within any.run) and the current date/time – oddly enough in the US format another sorry miss.
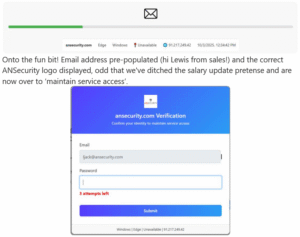
Finally after ‘entering’ the credentials 3 times we’re redirected to the domain https://ansecurity.com – which for us goes nowhere with www.ansecurity.com being the public facing domain. In the past we’ve seen such attacks be backed by something like Evilginx to meddler-in-the-middle the credentials and attempt MFA interception/bypass, something which we used to class as at least determined and high skilled threat actor but that has become so common we’re now classing it as also in the realm of determined but low skilled threat actors. We were almost sad to see no indication that the ‘credentials’ we provided in the sandbox were used with no failed sign-in attempts seen.
What can be done to prevent such attacks?
The phishing training companies will tell you that you need the best security awareness training, mail filtering companies will tell you that you need better mail filtering, and the firewall companies will say that you need great DNS/URL filtering. Meanwhile the real answer and the only one 100% effective (so far as we know!) against such an attack with just a single layer of protection is the implementation of phishing-resistant authentication with FIDO2. Be it Windows Hello for Business, or a hardware security key whenever you submit credentials with such a service the recipient of the identity (the website you are on) is checked and validated before anything is released. Speak to your ANSecurity account manager to learn how such a technology can be implemented in your own organisation.
Indicators of compromise
selfinglesdinamico.com[.]br
loginsupport.s-ed1.cloud.gcore[.]lu
