SECURE ACCESS SERVICE EDGE (SASE), IN THE CLEAR…
14 October
SASE is a collection of technologies which deliver consistently secure, reliable, and scalable connectivity to users working outside of HQs. It’s emergence as a field of networking & security has been accelerated by the adoption of SaaS/cloud delivered applications as well as the drive to home working.
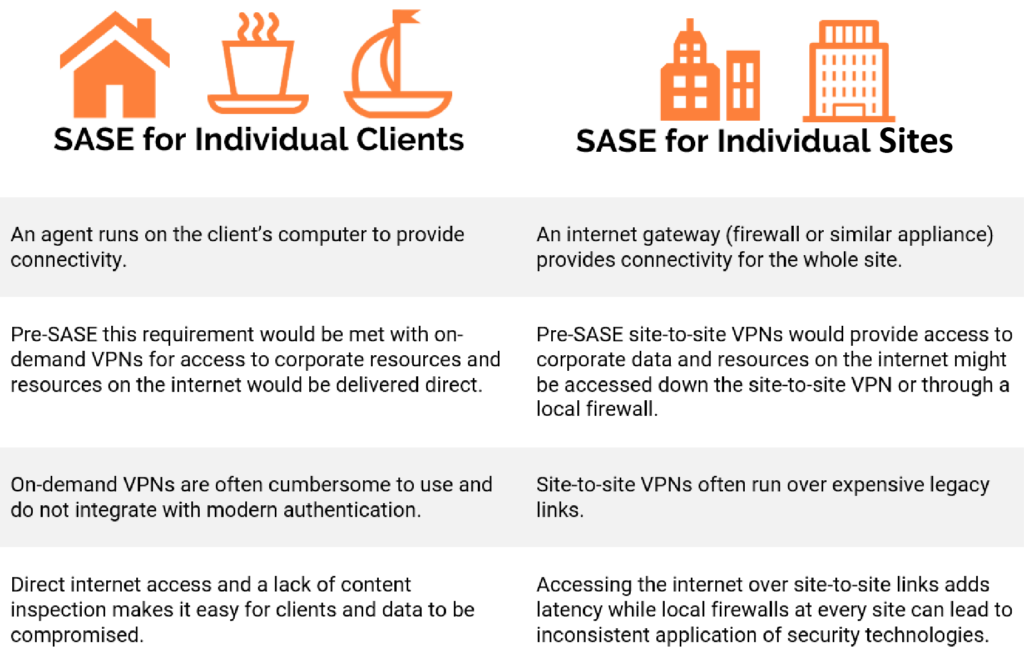
There are two main use cases covering client and site wide connections, the end goal of any SASE project should be to provide the same level of network security and connectivity to your users as if they were at your HQ.
As some organisations look to downsize or simplify their office estate, we have seen SASE being used to reduce the local infrastructure requirements. In one case the organisation has just an internet gateway and handful of network switches and wireless access points to provide a secure experience for their office of 80 users.
WHAT SHOULD I BE GETTING OUT OF SASE?
Much of the return on investment of a SASE solution is found in the reduction of disparate technologies. No more managing many different VPN services some which serve individual users and others site-to-site connections while also handling decryption and content inspection in separate appliances or tools. Aside from these core benefits you should also look to obtain the following features as part of any SASE platform.
Simplified connectivity
Legacy links between sites often come at much higher costs than modern broadband and might require specialised hardware or routing requirements, they are also often inflexible when it comes to bandwidth upgrades. With SASE remote sites now just require internet connectivity and a compatible gateway to receive the full breadth of security services that you might enjoy at an HQ.
For remote users on traditional VPNs they might encounter issues when making IPsec connections due to local firewalls blocking the required ports with no easy fall back option. Meanwhile, SASE services can adapt the connection type depending on the service provided to the client falling back to TLS for transport when required. As more users join the organisation or if there is a spike in demand SASE services can also easily increase their available bandwidth enabling IT to always adopt a ‘full-tunnel’ policy ensuring all traffic can be inspected.
Visibility
Organisations that don’t have the ability perform full-tunnel VPN will always have gaps in their visibility of user’s activities, SASE services light up this activity with inline application identification. This ability allows IT and decision makers to get a grip on Shadow-IT and ensure that access to unsanctioned services is restricted.
Network policy enforcement
By combining connectivity and policy rules on the same service SASE enables you to extend the Zero-Trust approach to network security that you might already have adopted at the HQ out to remote users and branch offices as well. By grouping together branches and even remote users under a single security area/zone you can easily build out rules that apply your policies consistently everywhere instead of having to manage multiple security appliances perhaps from multiple vendors at each remote site.
This policy enforcement can be taken to the next level by using client health monitoring to ensure that devices are patched, running approved AV, encrypted, and sanctioned before they are given access to sensitive resources.
Actionable metrics on service quality
The massive uptake of video conferencing has brought about a shift from using available throughput as the sole metric to base user experience on to also include latency and jitter. A Teams or Zoom call might only require a few megabits of throughput for high quality video and clear audio but high latency or variable jitter can quickly make for an unbearable experience.
With a particular focus on remote users SASE services build in ‘autonomous digital experience management’ (ADEM) to collect information and establish where in the network path issues might be occurring. This could be a simple case of identifying poor Wi-Fi strength and asking the user to move closer to their access point or even identifying issues with a mobile operator in a geographical area for users on 4 or 5G connections.
An often-forgotten aspect of modern video conferencing software is hardware acceleration. If your users are experiencing high CPU utilisation when on Teams calls it will be worth checking this link Hardware decoder and encoder driver recommendations – Microsoft Teams | Microsoft Docs to ensure your computers have the required hardware to perform hardware decoding/encoding.
Data loss prevention
As more data is pushed into SaaS services it can become harder to accurately track where it ends up let alone what data might be sent to unsanctioned applications. SASE platforms track data through native integrations to the APIs of sanctioned SaaS applications while also using network level decryption and inspection against tags, metadata and even the contents of documents. This ensures documents marked confidential or files containing personal information don’t make it to unsanctioned applications and result in the next headline of a data breach.
How does it work?
Having read this far you might be thinking all of this sounds very familiar, maybe a few acronyms like ZTNA (Zero-Trust network access), SWG (Secure Web Gateway) and SD-WAN (Software defined WAN) are on your mind, and you’d be right – SASE with its elements broken apart is nothing new.
However, the element that SASE brings to the table against all these point products is its single pane of glass for all these features instead of having to manage separate integrations.
When looking at individual clients the SASE platform will go through a process that looks something like this:
IS SASE RIGHT FOR ME?
Just as SaaS platforms scale from 10s to 10,000s of users SASE solutions do the same, instead organisations should consider if the feature set that they receive from their current services covers all visibility or policy enforcement requirements.
Your SASE maturity level
To work out your path to a SASE future it’s worth knowing where you are now and establish your desired end state and from there work out the time and services required to reach the end state. The scales below from 1 (least adoption of SASE) to 4 (full adoption of SASE) can be used to establish your next steps.
Authentication (applicable to individual users only)
- Single factor authentication only.
- Multi factor using HOTP/TOTP.
- Multi factor using modern authentication (App/push notification).
- Security certificate or Passwordless authentication.
Connectivity
- Legacy site-to-site services over expensive links and internet services break out locally with little/no inspection, remote users connect directly to services over insecure mechanisms (e.g. direct to Remote Desktop Servers).
- Remote sites use limited content filtering for local internet breakout, Individual users connect to on-premises services via on-demand VPNs connections to the internet break out locally.
- Remote sites use the same level of content filtering as HQ (with local security appliances), Individual users connect to on-premises and Internet services through full-tunnel VPNs.
- Remote site and individual users are provided with the same level of connectivity and content inspection as if they were at HQ.
Visibility
- No visibility into user or branch office traffic.
- Visibility is anecdotal, extensive log analysis is required to identify traffic flows.
- Some visibility but some traffic is excluded (e.g. to the internet in split-tunnel mode or decryption is not used).
- Full visibility into all traffic (including encrypted).
Policy enforcement
- When connected to the VPN (client or site-to-site) there is no policy enforcement.
- Policy enforcement is based on source/destination IPs and ports.
- Policy enforcement is based on application identification.
- Policy enforcement is based on multiple metrics including user identity and machine health.
Quality of experience
- No visibility into quality of experience.
- QoS is applied at branch offices, no visibility into individual user connections.
- Monitoring of available bandwidth and latency/jitter to common services at branch offices, no visibility into individual user connections.
- Full visibility and actionability into the quality of experience for all users and sites.
Image by rawpixel.com on Freepik