Key Insights from the 2025 Verizon Data Breach Investigations Report (DBIR)
25 April
The 2025 edition of Verizon’s Data Breach Investigations Report (DBIR) offers a deep dive into the state of cybersecurity. This year’s findings shine a spotlight on both the scale and sophistication of cyber threats impacting organisations today. With over 22,000 incidents analyzed, including 12,195 confirmed breaches, the report highlights the shifting trends to businesses of all sizes.
Here are the key insights you need to know:
System Intrusions Nearly Double
One of the most striking findings: System intrusion breaches now make up 53% of all breaches in the EMEA region—nearly doubling year-over-year. These aren’t just isolated ransomware events either. We’re talking multi-stage attacks involving credential harvesting, lateral movement, and data exfiltration. The sad fact is the problem of credential theft has been effectively solved through the use of strong authentication and ‘passwordless’ practices – the use of FIDO2 be in in software passkeys or hardware security keys is known to be highly effective at preventing even the most sophisticated credential theft attacks. However, organisations have been slow to adopt this now matured technology and even where it is adopted the lack of regular review and continuous investment in legacy systems holds back complete adoption.
Why it matters: Attackers are getting more coordinated and technical. Organisations can’t afford to rely on perimeter security alone.
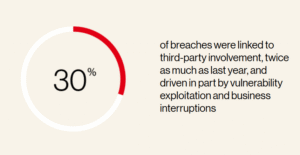
Third-Party Breaches on the Rise
Third-party risks are becoming front and center. 30% of EMEA breaches now involve partners, vendors, or supply chain entities—a jump from previous years.
Why it matters: You’re only as strong as your weakest link. Companies must vet their vendors more rigorously and adopt better third-party risk management frameworks. https://www.bbc.co.uk/news/articles/c9777v4m8zdo
The Human Element Still Dominates
Despite all the tech, humans remain a cybersecurity wildcard. 68% of breaches involved a human element, whether through social engineering, errors, or misuse.
Why it matters: Phishing and pretexting remain wildly effective. Regular test and evaluation of the efficacy of relevent and targeted cybersecurity training through simulated phishing tests are still crucial.
Vulnerability Exploits Up 34% Globally
The use of vulnerability exploits, particularly zero-days, has surged globally. Attackers are getting faster at weaponizing newly discovered vulnerabilities before organisations can patch them.
Why it matters: Delayed patching = open doors. A robust vulnerability management program is non-negotiable. Higher education and research organisations are particularly exposed to delays in the identification and remediation of software vulnerabilities, in recent Security Reviews conducted by our team these organisations were found to be more likely than other sectors to expose legacy systems to inbound connections from the Internet. Once compromised threat actors often found lateral movement and defence evasion to be trivial due to the lack of adoption of anti-malware or EDR agents on Linux servers.
Faster Breach Timelines, Slower Detection
Cybercriminals are breaking in faster than ever. In many cases, breaches happen within minutes—but discovery still takes days or even weeks.
Why it matters: Speed is the enemy. Tools like extended detection and response (XDR) and security information and event management (SIEM) systems can help reduce detection time. A surprising number of organisations still lack a mature incident response capability; in recent evaluations through our Threat Emulation service response times from 3rd party Security Operations Centres were sometimes as low as 15 minutes, but there are still vendors out there offering a 24×7 service which after 5:30pm on a Friday at best manages a 2 hour response to a high confidence detection of malicious activity.
Ransomware Still a Major Threat
Ransomware continues to be one of the most prevalent and destructive threats, particularly in EMEA. This year’s report shows that ransomware was involved in 24% of breaches globally, with many incidents overlapping with system intrusions and data theft.
Why it matters: It’s no longer just about encryption. Data theft and extortion have added new layers to ransomware attacks. A comprehensive response plan is essential.

Final Thoughts
The 2025 DBIR for EMEA is clear: the threat landscape is growing more complex, and attackers are evolving their methods quickly. Businesses can’t be passive. Proactive defense, informed strategies, and resilient infrastructures are the need of the hour.
What should organisations focus on?
-
Invest in modern threat detection and response tools
-
Improve third-party and supply chain security
-
Regularly patch systems and prioritise known vulnerabilities
-
Train staff to recognise and report threats
-
Develop and test incident response plans
- Test and evaluate the efficacy of your incident response capability
Read the full report for a deeper breakdown of breach trends and industry-specific insights:
2025 Verizon DBIR – EMEA
