What happens when you ‘click the link’ part 1 – sms
06 October
Despite mature technology (FIDO2) existing that would eliminate phishing (for credentials at least) already being available malicious attempts to gain credentials through social engineering continues, in these articles we will explore two real world failed attempts against ANSecurity staff.
Of note both instances are nothing ‘special’, in our determination a casual threat actor and a determined but low skilled threat actor, regardless of the skill level sometimes all it can take is someone caught off guard for sensitive details to be compromised. To explore both phishes we’ve used https://any.run/, a web based sandbox service that allows you to explore a link, email/document in a controlled manner. Be aware that when using such services any data you share is going to find it’s way to others.
Phishing for payment card details via text
See https://app.any.run/tasks/4f2db88a-d2ec-4e96-a6e5-dca35ab8ef3c for the sandbox investigation.
Our first phish was delivered by SMS text, a problem that OFCOM is well aware of and that the industry is yet to make serious progress on preventing. Loading the link in our sandbox we’re first greeted by a Cloudflare powered CAPTCHA, a method of ‘hiding’ the malicious content of the page behind from automated analysis by security products and vendors and as demonstrated by the domains reputation on VirusTotal an effective one as well.

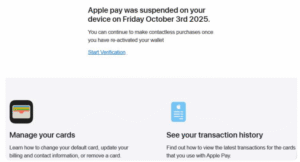
Next up an alert about ‘Apple pay’ being suspended – the date aligning with todays date, note that despite all the GenAI and LLMs in the world the threat actors still make small mistakes – it’s Apple Pay (correctly capitalised a little further down), all the same the toolkit they are using includes links to the legitimate Apple services but with the one key link to ‘Start Verification’.
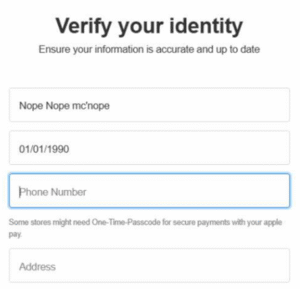
Next a simple identity details capture form, even if the threat actor doesn’t get a legitimate payment card they might at least get details which can be used to resell on. Note that we’re back to ‘apple pay’ over Apple Pay.
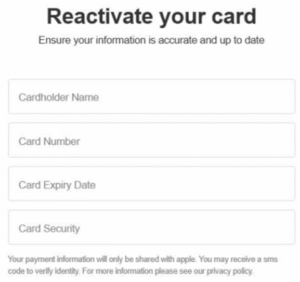
Finally, onto the good bit! The card details, interestingly the threat actor has included a checker for valid card numbers, https://www.canarytokens.org/nest/ to the rescue! Here we can generate payment card details that if used will trigger an email alert, something that at time of publishing (06/10/25) we’re yet to see used.
What can be done to prevent such attacks?
Preventing the actual delivery of malicious text messages is something that we as IT security professionals have very little control over, it’s something that the service providers are trying to chip away at and that Android/iOS is trying to build in. So what are we left with? Dare I say it’s good old user security awareness training, and perhaps network level defences by requiring all such mobile devices to connect to a VPN service which includes domain/URL filtering.
Perhaps the best way at helping to detect and prevent such attacks is by providing examples such as these to your users as part of interim updates to annual training – provide examples of what your users can expect to see and all being well trigger that ‘stop and think’ response.
